Cybersecurity has become a need in today's digital world as there is a continuous rise in cyberattacks and data breaches. This made organizations discover new ways of protecting their networks and data. One of the popular approaches to protect data is called Zero Trust Architecture, or ZTA for short. So, what is Zero Trust, and how can it improve cybersecurity? Let's understand it simply.
What is Zero Trust Architecture?
Zero Trust Architecture is designed in such a way that it will keep our data safe by following the rule of 'never trust and always verify.' This means that every person, device, or a system connected from any place will be considered suspicious until it is confirmed they are safe to trust.
It differs from the old model of security. In this traditional security model, all the systems or employees accessing the network were presumed to be trustworthy. The Zero Trust approach assumes that each request for access might be a threat, even though it is from a known or trusted source. So, instead of trusting devices or users based on where they are coming from, Zero Trust constantly checks and verifies each access attempt as if it were something illegitimate.
The Core Principles of Zero Trust Architecture
Zero Trust Architecture is based on a few core principles:
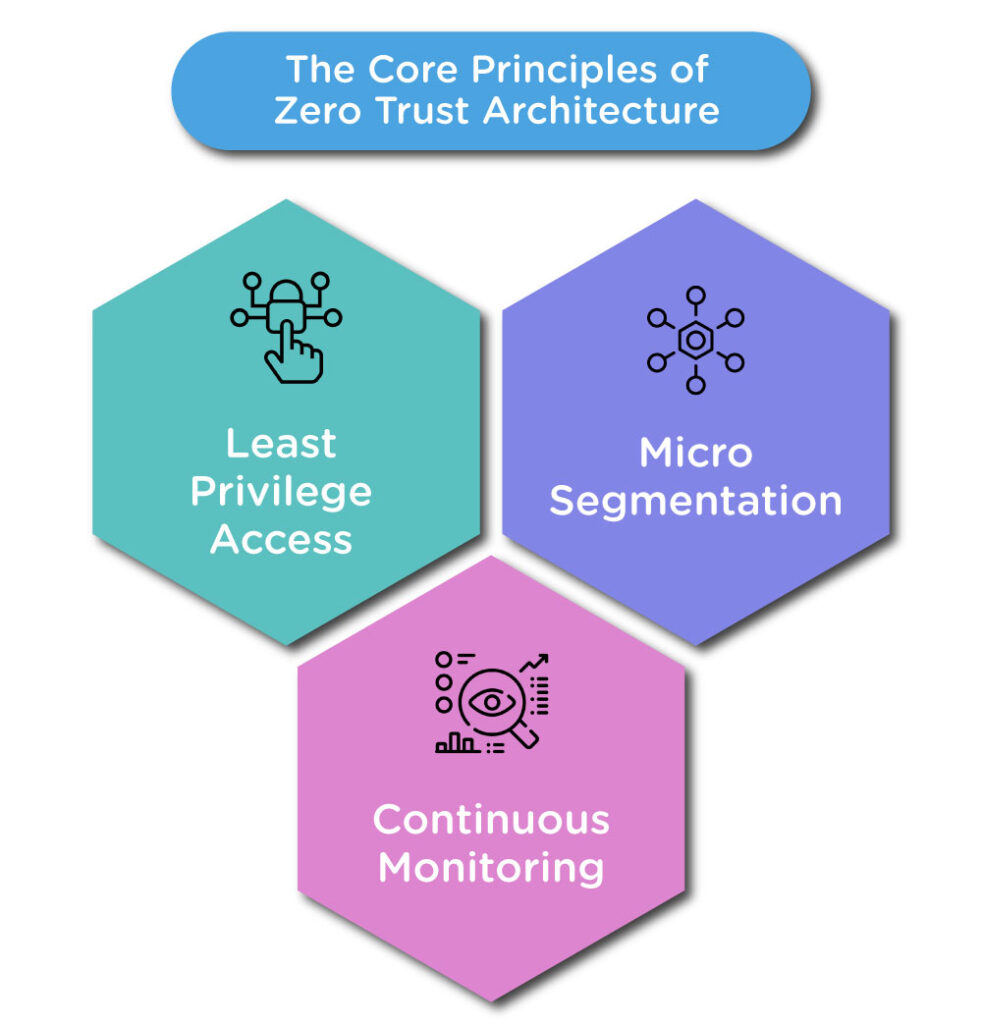
- Least Privilege Access: In Zero Trust, every user and device is authenticated and authorized before being allowed into any system or data from within or outside the network. This principle gives the users and the devices the minimum levels of access needed to do their jobs. If a user just needs to view a certain file or application, then they do not need all the access to the network.
- Micro-Segmentation: Divide the network into several isolated, tiny segments. This is a segment whose compromise can allow an attacker to access the segment alone but not beyond, meaning attacker cannot go further to access the rest of the system.
- Continuous Monitoring: Zero Trust doesn't stop here as access is allowed. It constantly tracks all the activity in the network to observe something suspicious in actions. For instance, the patterns of accessing resources at peculiar hours could call for attention to security breaches.
How Zero Trust Architecture Improves Cybersecurity
Now that we know what Zero Trust is, let's take a look at how it can improve cybersecurity:
- Reduces the Risk of Insider Threats: It reduces the possibility of insider threats. In traditional models, once someone is inside the network, they tend to be trusted to some extent. Each action, whether from an internal user, must be verified in Zero Trust. This makes it much harder for malicious insiders to cause damage as their actions are constantly being monitored and controlled.
- Limits Damage from Breaches: One of the major benefits of Zero Trust is that it reduces the damage done by a breach. With micro-segmentation, if an attacker gets into one part of the network, they can be blocked from reaching other sensitive areas. This will prevent serious damage, even if an attack happens.
- Improves Data Protection: Zero Trust architecture has the capacity to limit damage by a breach because an attacker gaining access to one part of the network may be stopped from reaching other sensitive areas through micro-segmentation. This would, therefore, prevent further widespread damage if the attack were successful in a certain part of the system.
- Better Protection Against Phishing and Malware: Most phishing attacks and malware rely on somehow managing to trick a user into granting access to an attacker. Therefore, with Zero Trust, even if the credentials of an end-user are compromised, the system will undertake additional checks and verification before access is granted. Comparatively, it becomes much harder for attackers to exploit stolen login information.
- Adapts to Modern Work Environments: It supports modern work environments. Most employees are now working remotely, accessing corporate networks with various devices. The classic security perimeter no longer works in these cases. Zero Trust is a perfect solution for modern work environments because it doesn't depend on the strength of a network perimeter. Instead, it continuously authenticates access requests from any location or device for safe access anywhere in the world where the employees are working.
- Faster Response to Threats: It would detect unusual or suspicious activities in real-time because it monitors the behavior of users and devices. Zero Trust allows security teams to respond faster to potential threats and prevent attacks before they cause significant harm.
Implementing Zero Trust Architecture in Your Organization
Implementing Zero Trust is not an easy task, especially in large organizations. It requires a lot of planning and the proper tools to verify every access request. Some of the steps an organization can undertake include:
- Identify Critical Assets: Identify what data and systems are critical to your business. These must be given the highest level of protection.
- Implement Multi-Factor Authentication: This is quite important as part of Zero Trust architecture because it provides an additional layer of verification when the access attempt is made by a user.
- Apply Micro-Segmentation: The aim here is to divide the network into smaller sections so that if an attacker gains access to one of the parts, they cannot move freely across the entire network.
- Monitor Continuously: Tools will be set to monitor and record all network activity. This provides for quick notice and response time to threats.
Final Words on Building Stronger Security Frameworks
Zero trust architecture helps organizations in keeping a watch on who is trying to access the information. It always checks who is trying to access specific information, reducing the possible harm from security breaches. Thus, users with permission and approved devices would eventually be allowed access to their very critical systems or data. Implementing Zero Trust gives benefits for necessary cybersecurity approaches at this connected stage of our digital world.
To read such more informative blogs, visit SecureITWorld!
FAQ
Q1: How does Zero Trust improve security?
Answer: Zero Trust enhances security by constantly verifying every user and device, irrespective of their location. With the assumption of no one as a default trust, it is hard for attackers to have unauthorized access, and this reduces the risk of data breaches.
Q2: What is Zero Trust in cybersecurity?
Answer: Zero Trust is a cybersecurity model that does not trust anyone, whether they are inside or outside the network. It continuously verifies the identity of users and devices before allowing access to any system or data.
Q3: What are the key concepts of Zero Trust Architecture?
Answer: Key concepts of Zero Trust are least privilege access, verifying every request, micro-segmentation, which is the segmentation of parts of the network, and continuous monitoring of activities for the detection of suspicious ones.
Also Read: The Best Cybersecurity Checklist to Protect Your Data