Ever noticed your coworkers' using apps and tools that aren't officially approved? This practice, known as shadow IT, is becoming increasingly common in today's workplaces. While it can enhance productivity and flexibility, it also raises important questions about security and compliance.
Let's dive into what shadow IT really means, along with its importance and pros and cons. Let's begin!
What Is Shadow IT?
The unapproved use of IT resources and features by staff members is referred to as "shadow IT." For instance, a worker who is unfamiliar with the organization's IT standards and procedures can download software to produce and share information inside the company without authorization.
This kind of conduct is inspected because it can compromise information security and risk private data, but there are also some good examples of shadow IT that highlight its benefits.
Importance of Shadow IT
The term "shadow IT" describes how employees of a company use unapproved programs and services. Although it presents serious security dangers, it also draws attention to vital elements of contemporary workplace dynamics.
Shadow IT's importance stems from its capacity to highlight deficiencies in official IT resources and highlight the demand for more adaptable, user-friendly solutions. When corporate technologies are thought to be insufficient, employees frequently look to shadow IT to improve productivity and collaboration.
Organizations can reevaluate their technology offerings by recognizing Shadow IT, which promotes a responsive and innovative culture. It pushes IT teams to interact with staff members, learn about their needs, and incorporate useful technologies into the official ecosystem.
By adopting Shadow IT, businesses may increase overall efficiency and promote technological innovation while simultaneously reducing risks through improved governance and utilizing insightful data.
Effective Shadow IT management might, therefore, result in an organizational environment that is more responsive and flexible.
Pros of Shadow IT
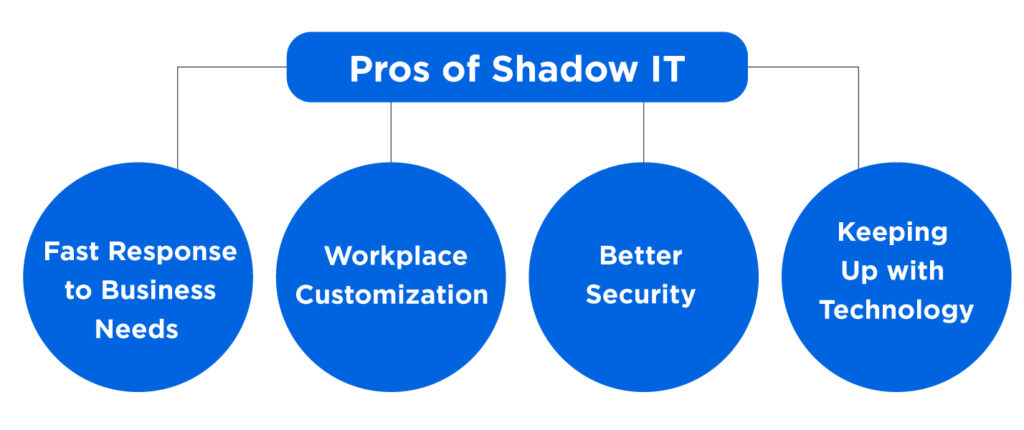
1. Fast Response to Business Needs
Workers don't have to wait for IT clearances to satisfy urgent requirements because they can utilize their own tools. To ensure a seamless transition during updates, they might, for example, download the required software in advance.
2. Workplace Customization
Shadow IT enables team members to modify their equipment to improve productivity. Increased productivity and job happiness, as well as the ability to retain talented workers who value individualized solutions, can result from this flexibility.
3. Keeping Up with Technology
Having the appropriate software is essential in businesses with intense competition. Without waiting for the IT department, staff members may swiftly install upgrades or new apps, keeping the company operational and compliant.
4. Better Security
When staff members decide to use updated software with improved security features, Shadow IT can strengthen security. Installing the most recent spam protection, for instance, can assist in addressing weaknesses in the organization's overall security plan.
Cons of Shadow IT
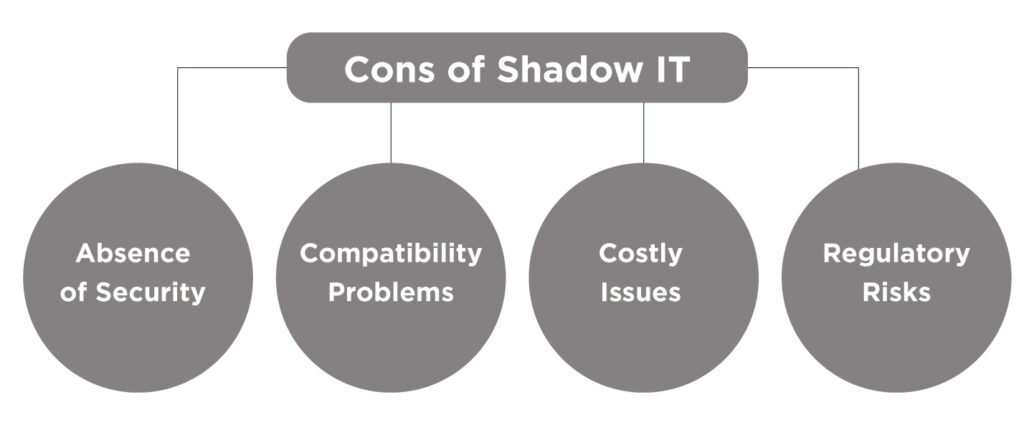
1. Absence of Security
Shadow IT may establish spaces where information is exchanged without enough supervision, endangering private data. This may result in illegal access and problems adhering to data protection regulations. Employee disregard for authorized IT tools could foster a culture in which disobedience to the law is accepted as the standard.
2. Compatibility Problems
Unauthorized employee use of tools may cause them to malfunction with the company's primary systems. Although these tools could be useful for some activities, they might be problematic when working with others or sharing data. Furthermore, there is a chance of data loss if crucial information is kept on these unauthorized systems because it may not be adequately protected.
3. Costly Issues
Security lapses caused by shadow IT can be highly costly. If a security breach happens, any productivity benefits could be lost, harming daily operations and consumer trust. Furthermore, workers can wind up purchasing tools that are identical to those already offered, depriving the business of the full potential of its authorized equipment.
4. Regulatory Risks
Using apps that are not permitted may result in legal issues. The business may be fined and have its brand harmed if it doesn't adhere to industry standards, particularly if sensitive data is handled improperly.
Conclusion
A balanced strategy is necessary to successfully navigate the shadow IT field. While it offers potential benefits like increased productivity and adaptability, it also presents serious security risks. By understanding both sides, organizations can create a safer, more efficient work environment that meets the needs of all employees.
We discussed the concept of shadow IT through this blog, and we hope it will help readers understand this concept and its pros and cons.
For more insightful and knowledgeable content, visit us at SecureITWorld.
Also Read: How Secure is Automotive Digital Identity?





