The best way to tackle any problem is to make an effort to fix it proactively. Given how many malpractices happen every day, it is really important to have a system that can detect threats and initiate a proper response towards them as soon as possible before they cause any harm to the network.
As the name suggests, automated threat detection is an automatic system that identifies any malignant activity that has the capacity to compromise the organization’s network or any assets and to initiate an appropriate response that cancels out the threat before it can take advantage of any weakness.
The speed of cyber threat development has reached unprecedented levels. Modern businesses along with their data confront continuous challenges from attacks on their information systems as well as hacking attempts. Organizations now use automated systems to identify and respond to rising security threats. Modern cybersecurity depends on these automated threat detection systems due to what they offer to protect operations. This paragraph examines systems in detail regarding their functionality. Let’s check it out!
Understanding Automated Threat Detection and Response Systems
Automated threat detection and response utilizes advanced security systems to detect along with analyze possible cybersecurity threats in real time through automated responses without human assistance. Enhanced security systems that incorporate artificial intelligence (AI) and machine learning (ML) along with data analytics enable automatic detection and instant reaction to suspicious events while replacing manual monitoring approaches of traditional security systems.
The main goal of automated threat detection systems involves minimizing the duration needed for threat discovery alongside subsequent response actions. Time remains essential to cybersecurity operations because delayed reactions bring about major data breaches and financial losses together with damaging reputation. Automation techniques enable prompt and accurate threat management which decreases human mistakes and fortifies total security structure.
How Does an Automated Threat Detection System Work?
Automated threat detection systems implement varied complex technologies and methodologies to function. Learn about the standard operations of these systems from the following breakdown:
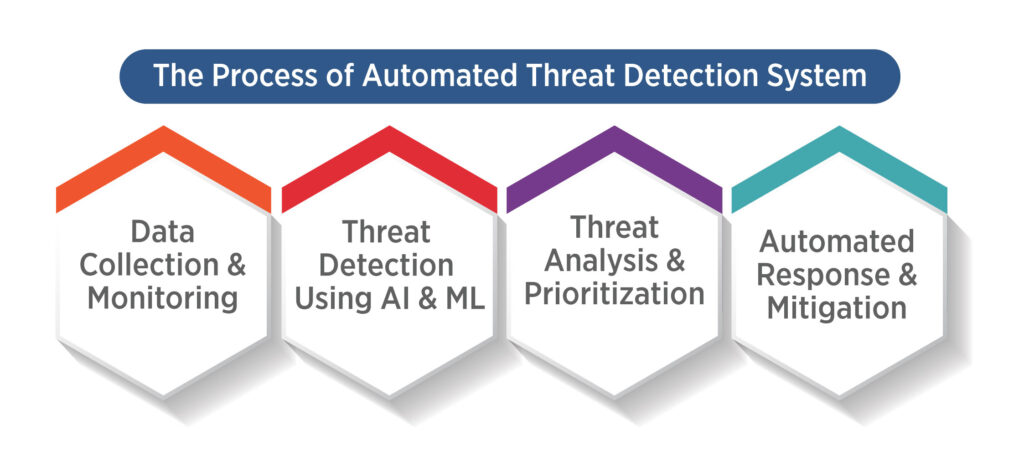
Data Collection and Monitoring
The system needs continuous observation of network traffic together with user activities and endpoint devices and application logs to start. Many monitoring sources feed data to the system which builds a reference pattern for standard activities. The system acquires a large volume of data through complete collection methods to conduct effective anomaly detection.
Threat Detection Using AI and ML
The system employs AI together with machine learning algorithms to examine collected data and detect abnormal conduct. The trained algorithms detect known security threats as well as zero-day vulnerabilities which represent previously undiscovered dangerous elements that do not appear in traditional databases.
System alerts appear when a user's account makes abnormal access attempts to sensitive files from unexpected locations against standard work hours. Automated threat detection achieves outstanding results in noticing anomalies which manual reviews commonly miss.
Threat Analysis and Prioritization
After threat detection the systems severity checks of potential threats. Analyzing how the threat interacts with original sources, as well as its potential effects on the system leads to threat assessment. Automated threat detection systems evaluate threats by their risk levels, so priority response is given to the most critical issues.
Automated Response and Mitigation
The automated response stands as the most vital concluding step in the security system. The system reacts to different threat types by running established action sequences which might include device segregation along with blocking harmful network addresses, user session interruption and malware change reversal in certain cases.
Automated responses are activated in real time through the system which creates a small opening for attackers. The ability to detect threats in real-time through automation stands as the critical factor behind its value in modern cybersecurity operations.
How Automatic Threat Identification Helps Businesses?
Businesses across industries are adopting automated threat detection systems to strengthen their cybersecurity strategies. Here are some key benefits these systems offer:
Quick Threat Reaction Time
Organizations must emphasize the need for speed while dealing with cyber threats. Automated systems have the ability to identify and respond to incidents in less than sixty seconds thus minimizing cyber threats perpetrators could inflict. The effective monitoring of all endpoints becomes complicated in large organizations so automated systems deliver immediate incident response silently.
Minimized Human Mistake Rate
We depend on human oversight systems for cybersecurity, but human errors become more common when handling complicated security threats. Automated systems' consistent operation, alongside their lack of fatigue, helps them detect threats with accuracy while diminishing oversight risk.
Optimized Expense Management
Organizations who choose initial implementation expenses for automated threat detection systems will achieve long-term cost savings. Businesses decrease their expenses through automatic threat identification by avoiding data breach costs while minimizing downtime requirements and needing fewer staff to monitor systems manually.
Flexible Growth Capacity
The growth in business operations leads to increased networks which expands potential attack opportunities. Security systems function automatically to expand infrastructure monitoring with no need for adding security personnel on a one-to-one basis.
Proactive Security Posture
Automated threat detection allows enterprises to handle security incidents proactively instead of answering events only after they take place. Businesses gain a higher degree of security resilience through their ability to detect potential attack points before they become actual threats exploited by attackers.
The Future of Automated Threat Detection and Response
Automated threat detection shows positive future indicators because technological advancements continue to progress. Multiple industries contribute to automatic threat identification evolution through the following developments:
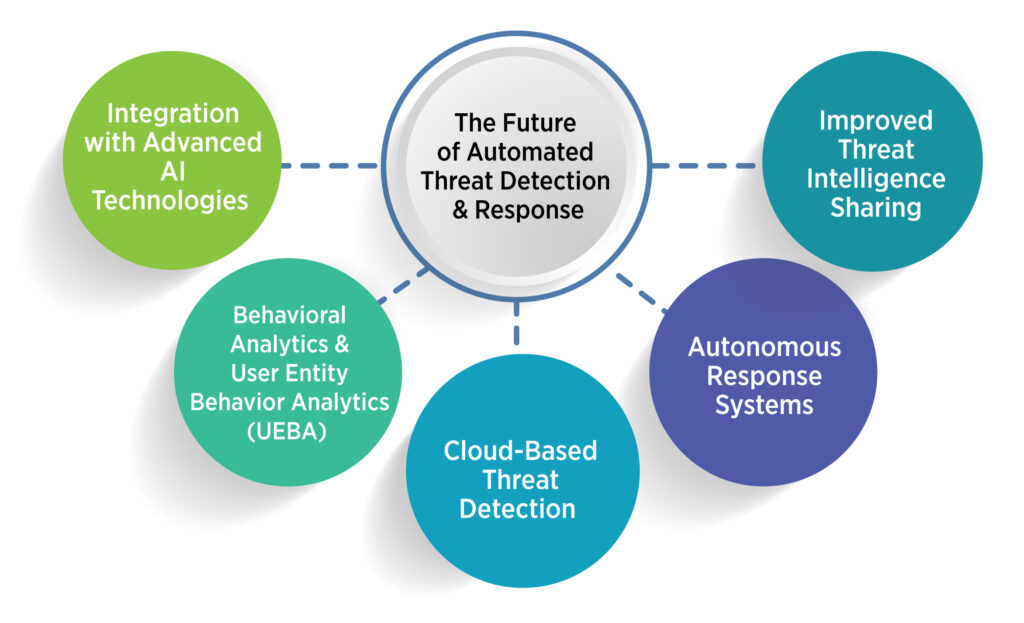
Integration with Advanced AI Technologies
The upcoming generation of systems will deploy advanced AI models which excel at identifying intricate attack patterns. Organizations will gain better threat prediction abilities through new systems which let them forecast upcoming attacks for proactive prevention.
Behavioral Analytics and User Entity Behavior Analytics (UEBA)
The detection of threats by automated systems will more frequently use behavior analysis methods to identify insider dangers and persistent threats (APTs). Such systems use behavioral analytics techniques to reveal hidden irregular patterns which heretical detection methods cannot detect.
Cloud-Based Threat Detection
Cloud-based threat detection will receive increased attention from automated systems because of the expansion of remote work and cloud computing. Through cloud-based threat detection remote network monitoring becomes possible thus achieving full security coverage in real time.
Autonomous Response Systems
The current reactive security systems will evolve into self-operating security systems that conduct complex decisions independently. The defense capability will gain improved sophistication which will decrease attack response times because of autonomous security systems.
Improved Threat Intelligence Sharing
Automation will expand its integration capabilities into worldwide threat intelligence networks. Such systems can achieve better threat detection through data sharing about security risks between multiple organizations and industries to build an organized cyber defense.
Concluding Remarks!
Businesses now protect themselves through automated threat detection procedures which have dramatically improved their cybersecurity strategies. The combination of AI and machine learning and automation enables these security systems to deliver fast and correct security solutions in a scalable manner across changing threats.
The adoption of automated threat detection systems has become vital business practice instead of remaining optional due to present-day requirements for cyber threat protection. Technology progress will make these systems more advanced which will produce unmatched security solutions for digital environments.
Learn more about threat detection with SecureITWorld!
Recommended For You:
Understanding Threat Intelligence and Its Importance for Advanced Security
Importance of Cybersecurity Training: How Businesses Can Prepare Employees to Combat Emerging Threats





