In today's digital world, every business and individual concerned with protecting sensitive data. With the rise of cyber threats and data breaches, organizations must take steps to protect their information. A strategy that works for data protection is the principle of least privilege (PoLP). The term is technical, but the concept is simple and helpful for organizations. In this blog, we will explore what the principle of least privilege is, how it works, and the benefits that it brings to data protection efforts.
What is the Principle of Least Privilege?
The principle of least privilege means providing access to the required access to the users to perform their job. Imagine the marketing department employee who doesn't ever have to look at the financial records to do the job. Under the principle of least privilege, that employee is unable to see those records. Thus, by limiting permissions, organizations decrease the risk of unauthorized access to sensitive data.
Why is PoLP Important?
It is easy to detect the attacks from various motives. Hackers can find weaknesses in the system, or insiders can unintentionally leak confidential information. Hacker’s principle of least privilege helps organizations avoid these risks to a large extent. If a user's account is compromised, the hacker is left with access to only some pieces of information rather than the whole system.
According to the report, in 2024, the global average cost of data breach reached USD4.88 Million. It is a 10% increase from the previous year. Thus, implementing PoLP will reduce the attack surface and related costs.
How Does PoLP Work?
Follow the given steps while applying the least-privilege principle.
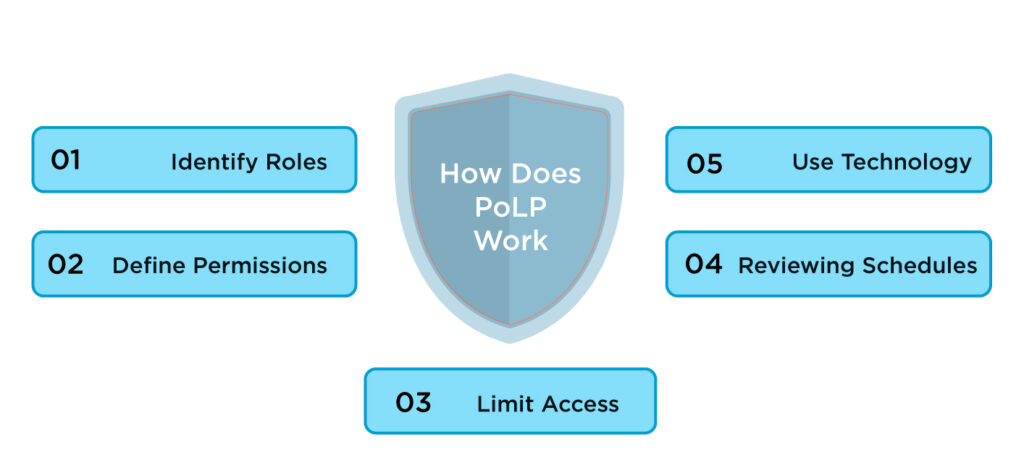
- Identify Roles: An organization needs to enumerate different roles in the company. Each role should have a clear knowledge of its responsibilities.
- Define Permissions: Next step is to define what data and what systems each role requires to perform adequately in order to do their job. This step elaborates the permissions required for each role.
- Limit Access: Once permissions are defined access should be limited accordingly. Access should only be given to whatever a user needs to carry out his job, not more.
- Reviewing Schedules: it is necessary to review user access regularly. The access permissions need to change or should be updated as employees leave the organization.
- Use Technology: Many tools and software help to manage user permissions. These tools automate the process of granting and revoking access to make the process easier.
Benefits of the Principle of Least Privilege
Reduced Chances of Data Breaches
PoLP reduces the risk of data breaches. Due to the restriction of access to limited information, an organization is not allowed by the unwanted users to view their confidential data. In this way, if a hacker accesses a user's account, then he will only find a small amount of data.
Minimize Internal Threats
Some breaches happen to be internal to an organization. People who work in an organization may misuse their access knowingly or unknowingly. Organizations reduce the possibility of insider threats through least privilege. Only as much information required by the employees for the job is accessible by them to minimize accidental exposure or misuse.
Improved Compliance
Many industries have regulations regarding data protection. For example, a health care related organization follows HIPAA, and a financial-related organization needs to follow the PCI DSS. PoLP facilitates better compliance with these standards. Limiting privileges helps to restrict access to sensitive information that is available only to those who need it and also simplifies compliance.
Increased Accountability
When access is limited, it becomes easier to track user actions. In case a data breach takes place, organizations will be in a position to easily identify who had access to the affected data. This makes the organization responsible because they will be able to know how this breach happened and what actions they can take to prevent this breach from happening again.
Cost Savings
Data Breaches can be costly to an organization. Fines, legal fees, and reputational damage are all considered liabilities due to a breach which may damage the reputation of the organization. An organization that enforces the principle of least privilege lowers the incidence of breaches and reduces the costs attached to it. Investing in data protection strategies like PoLP saves one money in the long run.
Summing Up!
The principle of least privilege is one of the important strategies for protecting data in today's digital world. So, restricting access to its users to only what is necessary may allow organizations to minimize the risks of a data breach, reduce potential internal threats, improve compliance, enhance accountability, and save costs. The expansion of cyber threats has increased the requirement of the principle of least privilege for organizations. The organizations that put this principle first will be able to better protect their sensitive data and retain the trust of customers and other stakeholders.
By knowing and putting into effect the principle of least privilege, you will always ensure a safe digital environment for your organization. It is one of the simplest ways to add value to your data protection strategy to keep the information safe.
To Know more how to secure data visit us at SecureITWorld!
You may also like to read: Cybersecurity Metrics Measuring the Safety of Your Data





