Have you ever questioned how hackers plan and carry out their attacks? Lockheed Martin's cyber kill chain (CKC) solves the puzzle by segmenting a hacker's path into distinct, manageable phases. With the aid of this robust framework, companies can remain ahead of the game by grasping how assaults develop from reconnaissance to monetization. Businesses may strengthen their defenses and prevent their vital data from getting into the wrong hands by being aware of the strategies scammers use.
This blog is all about the cyber kill chain, its history, and its stages. Let’s dive in!
Understanding the Cyber Kill Chain and Its History
The defense-in-depth, or castle and moat, strategy for cybersecurity is most likely something you have some familiarity with. Businesses continue to think about their information security using this concept. But, as businesses have developed, they have looked for new models that would help them better understand the ways in which cybercriminals work and how to effectively protect against them.
The cyber kill chain designed by Lockheed Martin. It was created as a component of the Intelligence Driven Defense concept. It is used to detect and stop cyberattacks and data exfiltration.
The military coined the phrase "kill chain" to describe the sequence of actions an opponent takes to strike a target. Lockheed Martin utilized this military model to outline the phases involved in today's cyberattacks in 2011. Security personnel who are aware of the seven steps an attack goes through are said to have a greater chance of preventing it or making it loud enough to be easily recognized.
After this model many models were proposed by different people, but this one is largely used model. It performs a fantastic job of concentrating on the human component of the cyber kill chain and is still among the more useful models. An industry that frequently prioritizes technology-driven threat intelligence over the dangers of social engineering and other human-based attack vectors would benefit from this.
The cyber kill chain model describes the steps involved in a breach by a cybercriminal or advanced persistent threat (APT) trying to get assets or sensitive data inside a security perimeter without authorization.
8 Steps of the Cybersecurity Kill Chain
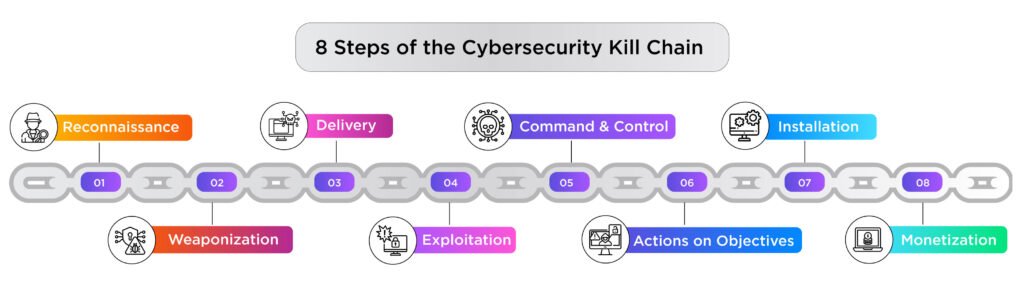
#1 Reconnaissance
The attacker gathers knowledge about the target at this stage, including network setups, critical persons, potential weaknesses, and security measures. Active scanning and probing of the target's system or passive methods like open-source intelligence (OSINT) collection might be used at this phase.
Attackers can use a variety of techniques to conduct reconnaissance both offline and online in order to learn more about their target's vulnerabilities. Penetration testing is also done at this stage to identify possible access points, which aids attackers in organizing their next course of action. Knowing reconnaissance enables defenders to foresee dangers and take action before they become more serious.
#2 Weaponization
The cyberkill chain's weaponization step starts once reconnaissance is complete and the attacker has acquired sufficient knowledge about possible targets and their weaknesses. The attacker develops or acquires an opposing payload, such as malware or a weaponized document, during this step with the intention of taking advantage of particular weaknesses found during the reconnaissance stage.
Weaponization may entail creating new malware or altering pre-existing tools for the assault. In order to accomplish the attacker's goals, this step also includes preparing the payload and maybe adding techniques to avoid detection by security software. Knowing weaponization enables defenders to foresee potential tools crafted by attackers.
#3 Delivery
The attacker sends the victim a harmful payload at the "Delivery" step of the cyber kill chain. This can happen via a number of channels, such as hacked websites, phishing emails, or malicious files. Delivery, which prepares the ground for carrying out the harmful payload, is essential to the attack's advancement.
#4 Exploitation
In the "Exploitation" step of the cyber kill chain, the malicious payload that was provided in the previous stage is executed by exploiting vulnerabilities found during reconnaissance. To take control of the target system, this may entail taking advantage of flaws in software, shoddy setups, or human mistakes.
#5 Command and Control
The phase where the attacker communicates with the compromised system or network is known as "Command and Control" (C2). Through this connectivity, the attacker may keep control of the hacked computers, issue instructions, and get data from them. It is a crucial phase because it permits continuous engagement and command of the target.
#6 Actions on Objectives
It represents the attacker's primary goal. This stage comes after the creation of cybercriminals' tools, their deployment on a target's network, and their system takeover. Exfiltration, encryption, system disruption, or data theft are objectives of the attacker.
#7 Installation
In this phase, the attacker attempts to use malware and other cyberweapons to infect the target's machines. Tools are set up at this point to allow the attacker to gain control of the system and steal important information. Attackers may use command-line interfaces, backdoors, and Trojan horses to gain access to the network. By establishing backdoors, the attacker can get access to the system.
#8 Monetization
Some security professionals support adding monetization as the eighth stage to the cyber kill chain. At this point, the cybercriminal's currency benefit from an attack is the main focus. Attackers may use the dark web to sell stolen data or demand ransom payments during the monetization phase in order to prevent the release or sale of sensitive material, including private information or trade secrets.
In what ways does the Cyber Kill Chain Concept Aid Businesses in Recognizing Cyberattacks?
The cyber kill chain concept offers an organized framework that assists businesses in:
- Imagine and understand the phases of an attack.
- Determine the attack's key spots and concentrate on them.
- Create defenses and plans to identify and remove threats at every turn.
- Improve incident response skills by identifying the point in the chain where an attack may be stopped or disrupted.
Empowering Your Business Against Cyber Threats!
The actions that attackers take are broken down by the cyberkill chain. This makes us understand cyber-attacks more appropriately. Businesses may identify vulnerabilities, strengthen defenses, and better handle attacks by knowing these phases. By enabling businesses to identify and stop assaults early, this framework lowers the possibility of damage and protects important data. The CKC is a crucial instrument for improving security tactics in the current digital era.
In the above blog, we made an effort to simplify the concept of the cyber kill chain for our readers. We hope this knowledge-giving content will assist you in making informed decisions for your business. For more cybersecurity-driven content, keep visiting us at SecureITWorld.
Recommended For You:





