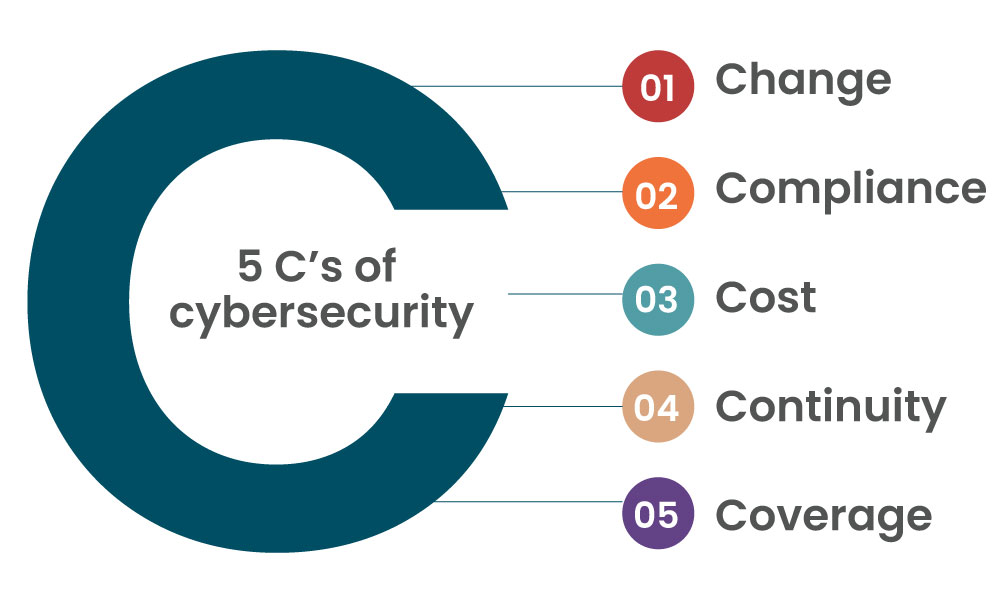
Cyber threats also grow as technology does. Businesses must have robust cybersecurity frameworks as hackers are always searching for weaknesses to exploit. The 5 C's of cybersecurity - come into play here. Let’s explore them with the hypothetical example of top-end hotel business.
Consider that - the top-end hotel chain Royal Haven provides seamless guest experiences via the use of smart technologies. Every feature, including automated payments, AI-powered guard services, and keyless room entrance, is made to be convenient. Keeping hotel systems and guest data secure from cyberattacks is a major issue since great technology comes with tremendous responsibility.
How 5 C’s of cybersecurity helped them in ensuring safety – let's see.
1. Change
The first “C” of cybersecurity is change.
As hackers are always coming up with new methods and tools to get around security measures, cyber threats are always changing. To stay ahead of new threats, companies need to be flexible and update their security procedures, systems, and technologies on a regular basis.
Now coming back to our circumstantial example, the security of Royal Haven is always changing along with cyber threats. Following an attempt by hackers to compromise its mobile key system, the hotel promptly upgraded its software and implemented additional security measures. Now, only the appropriate visitors were able to enter their rooms. This proves that change is necessary and important to protect your business.
2. Compliance
The second “C” of cybersecurity is compliance.
It means following the applicable laws, rules, and cybersecurity guidelines that are particular to your sector. In addition to preventing penalties and legal implications, compliance is essential for enhancing confidence with clients and business associates. Regulations like the Health Insurance Portability and Accountability Act (HIPAA) and the General Data Protection Regulation (GDPR) impose strict guidelines on how companies use, retain, and safeguard personal data.
As per our circumstantial example, how did Royal Haven implement this? It protects visitor data by adhering to rigid security regulations such as GDPR. By ensuring that sensitive information is kept safe, the hotel gains the trust of its visitors through encrypted payments and secure personal data storage. This ensures the safety of the hotel system.
3. Cost
The third “C” of cybersecurity is cost.
It refers to the costs associated with putting cybersecurity safeguards in place and keeping them up to date. The cost of a cyberattack is significantly higher than the cost of taking preventative action, despite the temptation to think of cybersecurity as an expensive burden.
Although it may appear costly to invest in cybersecurity, a data leak would cost far more. Once, Royal Haven's booking system was in danger of being shut down due to a cyberattack. The hotel's robust security procedures prevented the attack before it could do harm, perhaps saving millions of dollars in costs.
4. Continuity
The fourth “C” of cybersecurity is continuity.
Its main goal is to make sure your company can keep running even if there is a cyberattack. Because it reduces downtime, safeguards vital activities, and speeds up incident recovery, cyber resilience is an essential part of any cybersecurity plan.
Let’s see our hypothetical example - Royal Haven. It was prepared for a cyberattack that targeted its reservation system one day. Guests were able to check in and exit without any delays since backup servers immediately came online. Even during a crisis, efficient operations were guaranteed by careful preparation.
5. Coverage
The fifth “C” of cybersecurity is coverage.
It means making sure that every area of your company is covered by your cybersecurity efforts, from cloud services and third-party suppliers to internal systems and devices. Because hackers frequently target the weakest link in your security chain - which might be an unseen area like mobile devices or a third-party vendor - complete coverage is vital.
Cybersecurity encompasses more than just safeguarding one system. Online reservations, third-party payment systems, and smart room controls are all secured by Royal Haven. Frequent security audits keep the whole hotel network safe by identifying vulnerabilities before hackers do.
Cybersecurity - The Key to Trust and Long-Term Success!
Cybersecurity has become essential for companies that handle sensitive client data and depend on digital operations. Businesses like Royal Haven make sure that their systems are safe, that their operations run efficiently, and that their customers' trust is maintained by comprehending and putting the 5 C's of cybersecurity into practice.
Keep yourself safe and stay ahead! Invest in strong cybersecurity measures now to safeguard your company, win over customers, and guarantee long-term success. Don't hesitate - act right away!
For more helpful insights on cybersecurity and safety advice, keep learning through our blogs at SecureITWorld.
Also Read:
The Ultimate Guide to Cybersecurity Career
What is Zero Trust Architecture and How Does It Enhance Cybersecurity?





