Protecting company tools is now necessary due to the increasing culture of cyber-attacks. Isn’t it? Any laptop, smartphone, or tablet that is linked to a business's network might serve as an entry point for hackers. This is where endpoint security is useful.
It protects sensitive data by defending these devices from cyberattacks. Businesses run the danger of data breaches, monetary losses, and reputational harm if they don't implement adequate security measures.
This blog post will explain endpoint security, its process, and its importance to contemporary companies. You will have the best practices to maintain the security of your networks and devices in the end.
Let’s dive in!
Understanding Endpoint Security
Protecting end-user devices, including desktops, laptops, and mobile phones, against unwanted and dangerous software is known as endpoint security. It is also called endpoint protection.
Using these devices, staff personnel and team members access resources and connect to corporate networks. These devices must be protected by organizations to stop unauthorized access to networks, apps, and data repositories by third parties.
Working Process of Endpoint Protection
Endpoint security defends endpoints from cyber threats by utilizing a variety of procedures, services, and solutions. In order to prevent thieves from damaging devices, networks, and services, the initial endpoint security products were conventional antivirus and antimalware software.
Since then, endpoint protection has expanded to encompass more sophisticated, cloud-based, and all-inclusive solutions that assist in threat detection, investigation, and response, as well as in managing users, devices, and apps.
5 Key Elements of Endpoint Security
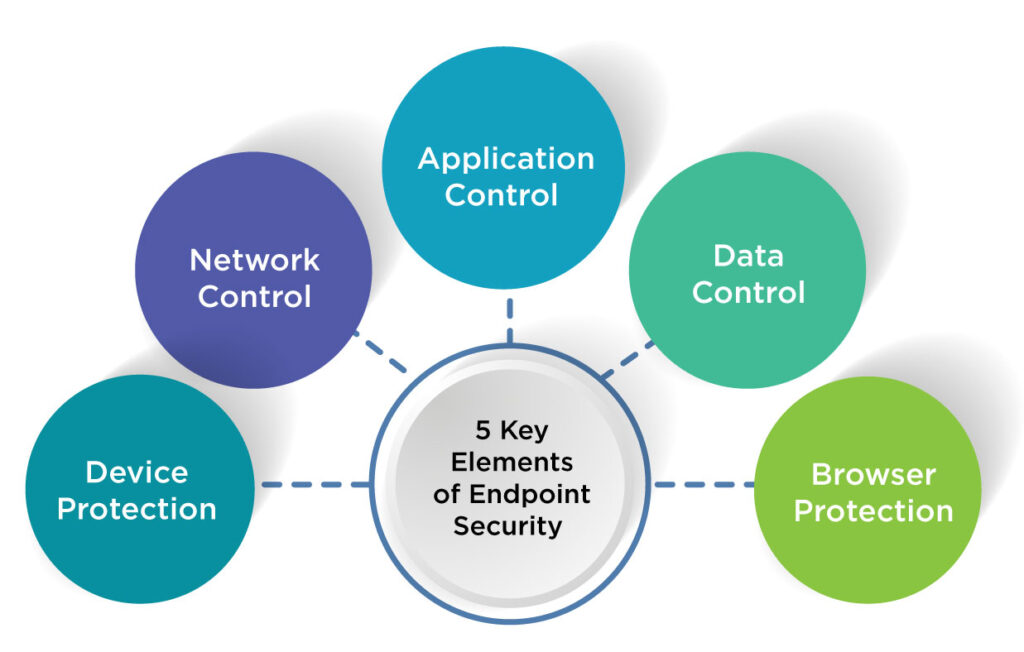
Organizations should think about whether their endpoint protection solution is complete enough to address threats from all angles, especially as the "bring your own device (BYOD)" culture and the number of mobile IoT devices in use continue to expand. Because of this, companies must comprehend the essential elements of an endpoint security system. Now let's examine the key components of an endpoint protection solution.
#1 Device Protection
Suspicious activity on endpoint devices is detected and investigated by the device protection component. One example of this is endpoint detection and response (EDR) tools, which monitor, record, and analyze endpoint events. It assists IT security teams in anticipating and addressing any attacks.
Endpoint security solutions offer malware protection and next-generation antivirus software for a variety of devices, eliminating emerging infections. The use of powerful analytics and machine learning by next-generation antiviruses makes it simpler to combat sophisticated phishing and ransomware threats that elude conventional antivirus software.
#2 Network Control
The component responsible for network control keeps track of, observes, and filters all incoming network traffic. It offers a feature that functions similarly to a firewall and aids in detecting, identifying, and managing possible security threats that might compromise the network of the organization.
#3 Application Control
The degree to which endpoints have control over network-enabled apps is known as the application control component. Integration with application servers is what distinguishes this, as it aids in identifying, tracking, and limiting endpoint access to these specific apps.
Application patching is another aspect of this component that aims to eradicate any security threats related to specific software programs. By keeping all endpoints, including PCs, servers, and apps, up to date, enterprises may benefit from enhanced security coverage.
#4 Data Control
Data handling across a network is controlled by the data control component. Both stored and in-transit data are included in this. The data control tool encrypts important or sensitive data to stop data breaches and enhance overall data security. When data is encrypted, it becomes unintelligible and inaccessible to hackers.
#5 Browser Protection
Endpoint security solutions use web filters to protect browsers. You may select which websites or content your users can view while connected to your network by using these filters.
Known as the principle of least privilege (POLP), this component provides privilege control functions. Businesses are able to provide users and processes with the bare minimum of resources required to do their activities. POLP eliminates local administrator permissions on PCs and servers, limiting access privileges to approved users and programs. This considerably lowers the company network's security threats.
The Advantages of an Endpoint Protection
- Protecting remote working policies, which allow productive work on any device
- Providing employees with safe endpoints and data access
- Safeguarding remote working guidelines so that productive work may be done on any device.
- Using an endpoint security platform to safeguard devices against hacker vulnerabilities.
- Preventing data theft and network unauthorized access by adjusting to advanced attack techniques.
- Identity protection through device security, which permits safe work independent of the employee's access to company information and resources.
6 Best Practices for Endpoint Security
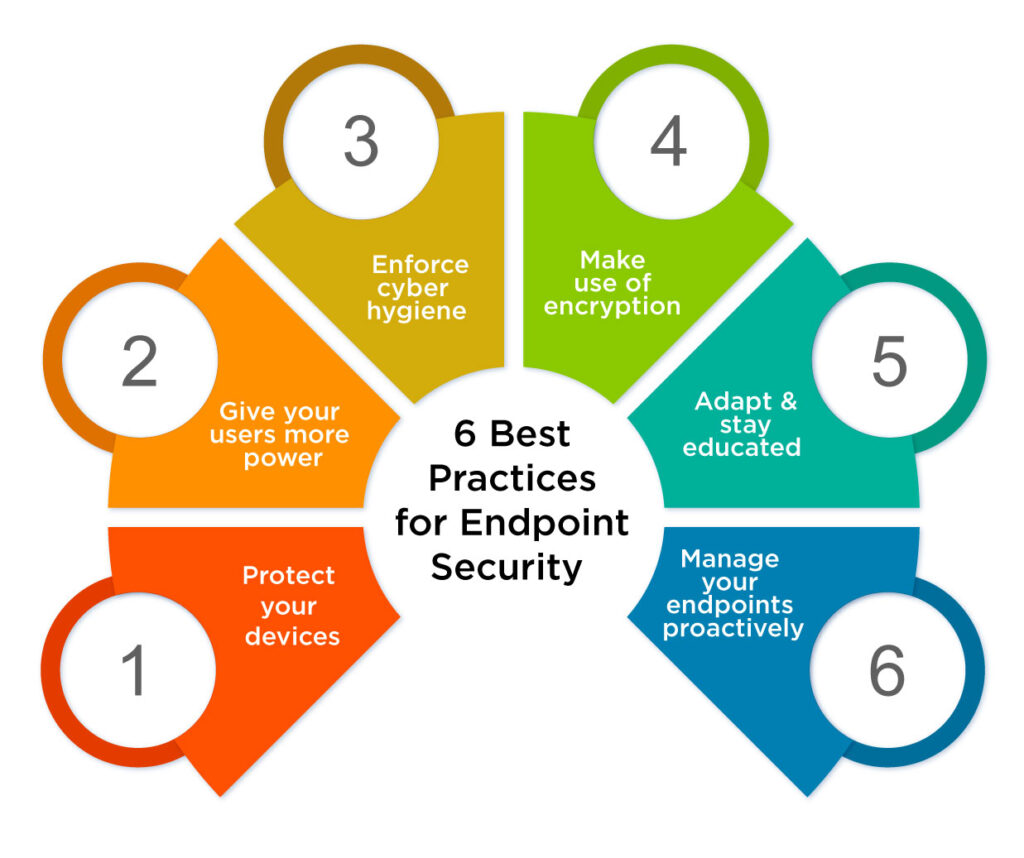
It's necessary to put in place an efficient endpoint protection or endpoint protection program to safeguard the vital infrastructure, data, and resources of your company. Here is a collection of the most important endpoint security recommended practices to get you started:
#1 Protect your devices
You can detect and stop attacks by installing firewalls, antivirus software, and antimalware software. You should routinely upgrade and patch operating systems and software apps on all connected devices to address known vulnerabilities. Implementing regulations that limit the use of unapproved hardware and software should also be a top focus.
#2 Give your users more power
Inform staff members about phishing scams and teach them not to click on dubious sites. To avoid any abuse, clearly define the reporting processes for questionable activities and conduct frequent audits of user access credentials.
#3 Enforce cyber hygiene
Make sure multi-factor authentication (MFA) and secure passwords are widely used.
#4 Make use of encryption
As remote and hybrid work environments become more common, encryption serves as an additional line of defense for private information while it's in transit and at rest.
#5 Adapt and stay educated
Since threats are constantly changing. It's critical to be informed of the most recent threats and vulnerabilities. Sign up for reliable sources, go to security seminars, and/or rely on a security vendor to keep you up to date on trends to ensure you have the threat intelligence you require.
#6 Manage your endpoints proactively
Endpoint activity should be regularly observed for questionable patterns. As possible dangers are found, rank them and take appropriate action. Additionally, you want to think about implementing an endpoint detection and response (EDR) solution. Real-time threat detection and response features provided by this kind of solution can assist you in promptly recognizing and addressing endpoint threats.
Securing the Future - Endpoint Protection Is a Must for Every Business!
As digital connections grow, organizations need to be proactive in protecting their data and equipment. Businesses may lower risks and stop cyber-attacks by putting robust security measures in place, such as encryption, multi-factor authentication, and ongoing monitoring. Maintaining protection also involves keeping up with the most recent security developments and updating systems on a regular basis.
Purchasing a trustworthy endpoint security solution guarantees uninterrupted business operations in addition to protecting your company. To create a more secure and robust online environment, start strengthening your endpoint security right now.
Act now to protect your company from online risks and keep ahead of hackers by putting robust endpoint protection measures in place! For more impactful and helpful content, keep visiting us at SecureITWorld.
Recommended For You:
Key Security Challenges and Solutions for Ensuring Data Privacy on Internet of Things (IoT)





